Get in Touch
Windows Internet Key Exchange remote code execution vulnerability
Target Industry
Multiline Retail, Industrial Conglomerates, Government, Financial Services, IT Services, E-Commerce.
Overview
Severity level: Critical – Exploitation of the vulnerability likely results in root-level compromise of servers or infrastructure devices.
Active exploits targeting Windows Internet Key Exchange (IKE) Protocol Extensions have been observed in the wild by security researchers from the Singaporean cybersecurity research organisation, CYFIRMA. The affected vulnerability, allocated CVE-2022-34721 by Microsoft, concerns unknown code in the IKE Protocol Extensions component running on vulnerable Windows OS servers, and thereby faciliates remote code exection (RCE) on the target systems. The observed vulnerability is limited to the IKEv1 protocol with IKEv2 unaffected, however all Windows Servers accept both V1 and V2 packets, resulting in a “critical” severity designation.
CYFIRMA researchers have confirmed in proof-of-concept activity that the exploit leverages a memory corruption issue with the svchost of the vulnerable system. Memory corruption occurs when Page Heap (a debugging plug-in) in the system is enabled for the IKE process. The executable process hosting the IKE protocol was shown to crash whilst attempting to read data beyond an allocated buffer.
Attacks utilising the exploit are supected to have begun on 6th September 2022, in a campaign termed “流血你”, translating to “bleed you”. This activity is suspected to have been conducted by unknown Chinese threat actors in potential collaboration with Russian cybercrime groups.
Impact
Compromise may result in RCE in the environment, which could allow a threat actor to gain control of the targeted system and thereby execute malicious code, escalate privileges, move laterally or exfiltrate data. These capabilities can facilitate data theft, extortion, ransomware attacks, any of which would be likely to result in significant operational disruption, financial loss and possible reputational damage.
Vulnerability Detection
The following commands will return the running status of any potentially vulnerable system running the IKE and AuthIP IPsec Keying Modules:
Powershell: C:\> Get-Service Ikeext
Cmd: C:\> sc query ikeext
Please note that running these queries could have negative affects on IPSec functionality, as stopping or disabling the IKEEXT service will disable IKE and AuthIP key exchange with peer computers.
Affected Products
Windows Server 2008 – Start Version: r2 End Version: r2
Windows Server 202 – Start Version: r2 End Version: r2
Windows 10 – Start Version: 1607 End Version: 1607
Windows 8.1
Windows Server 2016
Windows Server 2008
Windows 7
Windows rt 8.1
Windows 10 – Start Version: 20h2 End Version: 20h2
Windows 10 – Start Version: 21h1 End Version: 21h1
Windows 10 – Start Version: 21h2 End Version: 21h2
Windows 10 – Start Version: 1809 End Version: 1809
Windows 10
Windows 11
Windows 11
Windows Server 2019
Windows Server 2022
Windows Server 2022
Containment, Mitigations & Remediations
We strongly recommend updating your system with the September 2022 Microsoft security updates. We advise that all patches are routinely applied to all systems in order to mitigtate against the possibility of zero-day attacks.
Indicators of Compromise
No IOCs released.
Threat Landscape
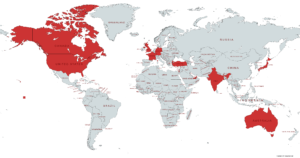
Attacks exploiting CVE-2022-34721 have been observed primarily targeting entites located in Western nations, including the UK, the US, Canada, Australia, France and Germany. With Russian and Chinese threat groups suspected of exploting this vulnerability, there is a realistic possibility that organisations and sectors facing any extant threat from Russian or Chinese actors may be targeted. It can also be expected that opportunistic threat actors will continue to attempt exploitation of unpatched assets, capitalising on any period in which a target organisation’s mitigation of vulnerable systems is slow or delayed.
Threat Group
On the basis of the discovery of the campaign name ““流血你” and reporting by CYFIRMA, we assess a realistic possibility that an unknown Mandarin-speaking threat group, and possibly FIN7, has exploited this vulnerability.
Mitre Methodologies
T1059.006 – Command and Scripting Interpreter: Python
T1495 – Firmware Corruption
T1190 – Exploit Public-Facing Application
T1569 – System Services: Service Execution
Further Information
Microsoft Update Guide – CVE-2022-34721
Github – 78 Research Lab – CVE-2022-34721 Proof of Concept
CYFIRMA – Windows Internet Key Exchange (IKE) Remote Code Execution Vulnerability Analysis
MITRE ATT&CK – FIN7

