Get in Touch
Microsoft Patch Tuesday March 2024
Target Industry
Indiscriminate, opportunistic targeting.
Overview
Microsoft March 2024 Patch Tuesday: One critical remote code execution (RCE) vulnerability and four browser flaws were addressed as a part of 60 total security vulnerabilities addressed by Microsoft. A summary of the highlighted vulnerabilities has been outlined below:
A critical RCE escape vulnerability in the Windows Hyper-V virtual machine (VM), tracked as [CVE-2024-21407], has been ranked with a high-severity score (CVSS 3.1 score: 8.1). The flaw requires a threat actor to initially gather information specific to the target environment and conduct unspecified preparations prior to exploitation efforts.
One Exchange vulnerability was disclosed in this month’s patch release. The flaw, tracked as [CVE-2024-26198] (CVSS:3.1 score: 8.8 ) is an RCE security issue which allows a threat actor to place a specially crafted DLL file into a network share or other file-sharing resource, subsequently luring the target to interact with it.
SharePoint received a patch for an arbitrary code execution flaw, tracked as [CVE-2024-21426](CVE-2024-21426), which Microsoft has described as an RCE issue allowing threat actors to lure targets to open a malicious file.
This month has seen the disclosure of an Azure Kubernetes vulnerability, tracked as [CVE-2024-21400]. It could allow an unauthenticated threat actor to hijack containers, with additional consequences. These include credential theft and resource impact out with the management controls of the Azure Kubernetes Service Confidential Containers (AKSCC).
Microsoft also released what they describe as a “compressed folder tampering vulnerability” in Windows 11. Successful exploitation of the flaw, tracked as [CVE-2024-26185], requires a threat actor to lure a target into opening a specially crafted file. Although the outcome of successful exploitation remains unclear, there is a realistic possibility that this security issue could be leveraged to modify a compressed folder but not necessarily read from it.
Impact
It is likely that successful exploitation of the vulnerabilities outlined within the March 2024 Microsoft Patch Tuesday disclosure could result in the total loss of confidentiality, integrity, and availability of data within target systems. In addition, it should be noted that exploitation of CVE-2024-21426 could lead to downtime for the target environment.
Vulnerability Detection
Security patches for these vulnerabilities have been released by Microsoft. Previous product versions therefore remain vulnerable to potential exploitation.
Affected Products
A full list of the affected products pertaining to the March 2024 Patch Tuesday can be found on the Microsoft March 2024 Security Update page.
Containment, Mitigations & Remediations
It is strongly recommended that the relevant security patches are applied to the respective Microsoft products as soon as possible. The patches can be found directly at the Microsoft Patch Tuesday March 2024 Security Guide.
Indicators of Compromise
No specific Indicators of Compromise (IoCs) are available currently.
Threat Landscape
Last month, Microsoft published remediations for 73 security flaws within the February 2024 Patch Tuesday release, including two zero-day flaws and thirty RCE vulnerabilities. Moving into the March disclosure, RCE and privilege escalation vulnerabilities continue to be leading attack vectors accounting for 30% and 40% of disclosed issues respectively, a trend that has continued from last month. Overall, the March 2024 Patch Tuesday disclosure resulted in the release of fewer vulnerabilities correlating to a lower number of products compared to recent times, a trend that has been detected to have emerged since the November 2023 Patch Tuesday release.
Threat Group
No attribution to specific threat actors or groups has been identified at the time of writing.
Mitre Methodologies
Tactics:
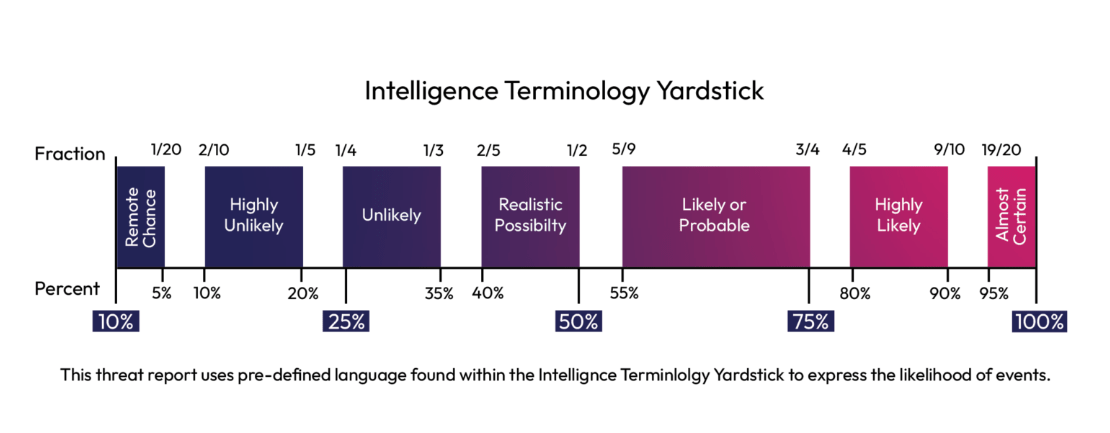
Intelligence Terminology Yardstick