Get in Touch
Housing associations exposed to increased waterhole attacks
Target Industry
Housing associations and the construction sector.
Overview
Severity level: High – Compromise may result in the loss of confidentiality and integrity of data in the first instance.
Over the past week, Threat Intelligence (TI) has tracked increased malicious activity involving the housing association and construction sectors. The chosen criminal methodology behind these attacks is via the ‘waterhole’ or ‘search engine optimisation poisoning’ style of compromise.
In most instances waterhole attacks employ social engineering against the victim, tracking online movements, thereby generating patterns of the most frequently visited sites. The attacker then targets these sites via known exploits or a zero-day and waits for the target to visit the now compromised site on their own accord, thus leading to a potential third-party compromise.
During an ongoing investigation, TI has discovered a waterhole instance directly targeting those organisations in these sectors.
In this attack, two instances of malware have been uncovered. The Cobalt Strike post-exploitation tool and Gootkit PowerShell malware.
Impact
Compromised websites containing initial access points for waterhole attacks are difficult to detect as they fall outside of regular security monitoring patterns. This, therefore, creates the issue that detection is only achieved once initial exploitation has occurred.
Both Cobalt Strike and Gootkit pose a significant threat to customer systems and networks, as a successful attack may result in the loss of confidentiality and integrity of data in the first instance.
Vulnerability Detection
Both Gootkit and Cobalt Strike should be detected and flagged as high-level alerts with an up-to-date endpoint detection and response (EDR) solution such as Microsoft Defender.
Affected Products
Microsoft PowerShell.
Containment, Mitigations & Remediations
Customers are strongly advised to remove or deny users that do not require the functionality and access to execute PowerShell commands.
Customers are also advised to actively use up-to-date EDR solutions such as Microsoft Defender to detect and stop attempts of compromise.
Indicators of Compromise
During the initial investigation of a waterhole-based compromise, multiple IOCs have been exposed including malicious Internet Protocols (IPs), domains and shell scripts.
Cobalt Strike:
146.70.53[.]165, IP has three active ports – 22, 80 and 443. Cobalt Strike was detected via port 443.
Based on the multiple correlating OSINT reports by RedPacket Security and C2IntelFeedBot and an investigation conducted by the Quorum Cyber Incident Response (IR) and TI teams, it is almost certain that 146.70.53[.]165 is directly associated with Cobalt Strike.
Cobalt Strike hashes:
d78bdef2ec67cb29a28d57e1579bb6f359d3dfcd7602d64d0673311ad83edbb2
2fe580c0325d342b10d138754e4c32dd50eb928fb4431b8acbbd4edc08c13c9f
0b36a30637adb49d6f710d7f87bec6b58f3e25544ef78f4d3f8403f833d60333
6334604f7ee7686bbeb9d55dc1b4e9a0e4cfa84bae2663b243c190d0aed29e84
b67842f5eef61f0d7baf1737496402d667cf8d8c5f3e75f9a58fdc55592068c0
e95a11233017f2a255053b36db7dca6b5415c9131875bddc072ac33ddb0277fe
02378db7c06f4437708154263156d78519bf2ddbf6d38935ac7c1e2275f0b3cd
5bc577ea217f36fd87881e132b6d46943fd2bbbe93d9fe5399eb3612a0fdf7e9
7099147594fd30ddb8e0ffc8be7b04069b60eaaef045671bb7cf3f36490d3dcf
af2129d4f31cf7872742c7753af185d45d3c76f7179369ed997023950207a911
d83b09edd7f7bc8cc6041ca79efab0762a31fffdf3758ab60cbfd130969aee1e
e178a801e1c561de32ee9fe90065d5c6e4430e40d71de58c307e28d8f561a863
f9d80edc05234b5a5b37b45e5534edfdd61729c5ff02aed8cde6e503e8387fed
Gootkit:
Investigation of associated PowerShell scripts highlight Gootkit affiliation to the following domains:
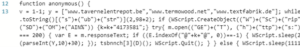
Domain 1: www[.]tavernelentrepot[.]be
IP: 188.165.196[.]209
Country: France
City: Roubaix
Domain 2: www[.]termowood[.]net
IP: 93.113.63[.]253
Country: Turkey
City: Denizli
Domain 3: www[.]textfabrik[.]de
IP: 83.169.20[.]225
Country: France
City: Strasbourg
Investigations have connected all three domains listed above to Gootkit malware activity. This, combined with OSINT reporting, suggests that these domains are highly likely affiliated with the Gootkit compromise on the victim system.
Additional Gootkit C2 domains:
theodoraross[.]com/xml.php
theairtrekstory[.]com/xml.php
tavernelentrepot[.]be/xml.php
Gootkit hashes:
973d0318f9d9aec575db054ac9a99d96ff34121473165b10dfba60552a8beed4
0e451125eaebac5760c2f3f24cc8112345013597fb6d1b7b1c167001b17d3f9f
60aef1b657e6c701f88fc1af6f56f93727a8f4af2d1001ddfa23e016258e333f
327916a876fa7541f8a1aad3c2270c2aec913bc8898273d545dc37a85ef7307f
d0e075a9346acbeca7095df2fc5e7c28909961184078e251f737f09b8ef892b6
a7e363887e9a7cc7f8de630b12005813cb83d6e3fc3980f735df35dccf5a1341
6e2cb88bf16f18b22f58603ddca81750
074d39af2df879c713406b00c04ca79e
60e079ec28d47ef85e93039c21afd19c
b760f973a9b78490766a5fe3c92bc5d0
3f4b1c4f7ce699382d5f126a512c6bbf
Threat Landscape
The popularity of the waterhole attack against the housing association and construction sectors is unlikely to diminish over the remainder of 2022 and will likely continue to be a mainstay tactic of cybercriminals targeting the sector throughout 2023. It is a realistic possibility that this tactic has grown in popularity because businesses across the private sector have significantly improved phishing awareness among their employees, making phishing attacks less effective. Attackers are likely moving to waterhole tactics to evade initial user detection. These attacks are likely to be from financially motivated criminal organisation networks.
Threat Group
No specific threat groups have been connected to recent threat activities.y
Mitre Methodologies
Cobalt Strike TTPs
Gootkit TTPs:
- T1591.002 – Gather Victim Org Information: Business Relationships
- T1189 – Drive-by Compromise
- T1546.013 – Event Triggered Execution: PowerShell Profile
- T1059.001 – Command and Scripting Interpreter: PowerShell
Further Information
During the TI investigation of a Microsoft Defender alert of Gootkit it was noticed that the adversary has likely spoofed the content section to imitate a legitimate Microsoft programme. This suggests that the adversary is sophisticated and well versed in PowerShell manipulation.
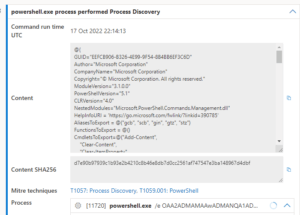
DFIR – Gootkit
Trend Micro – Gootkit delivery of Cobalt Strike

