MCAS Series (Part 2): Conditional Access App Control
Published: 7th July 2020 | In: Tech Blog
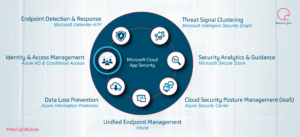
Following on from our first instalment of this Microsoft Cloud App Security (MCAS) series, we are going to provide a how-to on the configuration of MCAS and integrate it with some other pre-existing controls to provide rich visibility, complete control over data travel and discover applications that are being used within your business (see figure 1).
In this blog, we will be discussing the traditional method of deploying conditional access policies within Azure AD and how you can leverage the Microsoft Cloud App Security Broker (CASB) to elevate your security controls and security posture. Together, they allow you to take control of your cloud environment and respond to security threats in real-time.
Conditional Access App Control: What Benefits Can You Attain by Deploying this Control?
Conditional access policies are not a new concept. They are part of the modern security perimeter that utilises identity signals as part of their access control decisions. Signals, such as user and location, device and application can be utilised to determine levels of access control.
Conditional access [1] is the tool used by Azure Active Directory to decide how an organisation policy is deployed and which users are affected. Cloud Access App Control enables administrators to direct users requests and responses through the CASB rather than directly with the application. An additional layer of security is therefore created allowing an administrator to create policies to limit user actions based on the user session.
Conditional App Access Policies
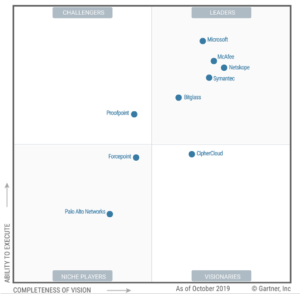
CASB solutions have one objective: to enforce security and governance. The market for these tools has grown exponentially, with the market forecast to reach 870 million U.S. dollars in size worldwide in 2019 [2]. Gartner named Microsoft a leader based on its completeness of vision and ability to execute in the CASB market in 2019. They were also identified as the strongest in execution [3] (see figure 2).
In the previous blog in this series, we discussed how many cloud applications are in use within an organisation without the knowledge or sign-off from internal IT teams. CASB’s are paramount in ensuring secure access and protecting the flow of sensitive data with a consistent set of controls by using session and access policies.
Now we’ll discuss how to configure applications to be forced to go through the Cloud App Security Broker and how to verify this has been achieved successfully.
For more information on licensing, please refer to the Microsoft Cloud App Security licensing guide at www.aka.ms/mcaslicensing
Set-up Conditional Access in Azure AD
When a company is looking to first deploy Cloud Access App it is important to monitor user activity to understand what is deemed normal for your environment and base your user controls around this. The following example will show a user accessing dropbox from a browser session being forced through the cloud app security broker. In this example, we will verify this has been achieved and the benefits of doing this.
NB: The next blog post in this series will show how to configure these benefits with a particular focus on using DLP policies to stop users from downloading confidential data on unmanaged devices.
Configuration Steps:
- Open the Azure Portal and navigate to Azure Active Directory > Conditional Access > Policies, and open the Conditional Access – Policies blade:
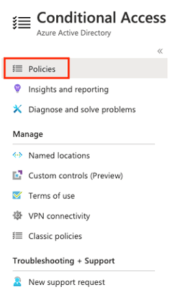
- On the Conditional Access – Policies blade, click ‘New policy’ to open the new blade:

- On the new blade, select the users and groups assignment to open the ‘Users and groups’ blade. On ‘Include’ tab of this blade, select ‘All Users’. For the purpose of this demo, I have only applied this policy to my account (see figure 5).
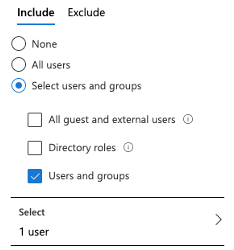
To deploy this against everyone in your organisation: select ‘All users’. Similarly, to exclude users: click on the ‘Exclude’ tab.
- On the new blade, select the Cloud apps or actions assignment. On the include tab, for the purpose of this blog post, we select, select apps and search for Dropbox for Business (see figure 6).
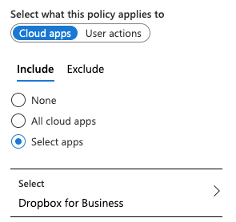
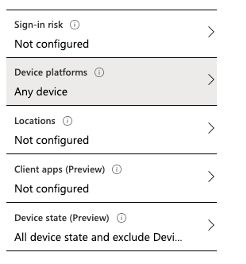
- On the new blade, select the conditions assignment and, for this example, we are only interested in selecting the device platform section. We then select any device and select yes to configure. This means no matter which device I use, all dropbox browser sessions will be monitored via Cloud App Security (see figure 7).
- Lastly, on the new blade, select the Session assignment and select Use Conditional Access App Control. For the purpose of just monitoring activities in this example, select Monitor only (see figure 8).
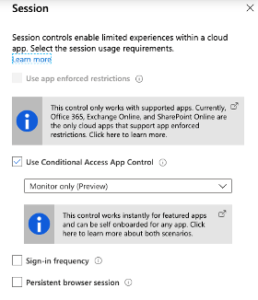
This is the section you would configure blocking downloads for users or using a custom policy which would be controlled via access and session policies within MCAS portal.
Verification
Now our conditional policy is set up, we want to confirm that users are being directed to the application through Cloud App Security. For comparison, this example will demonstrate a user logging into dropbox without the conditional access policy enabled (see figure 9) and vice versa (see figure 10).
Not Enabled
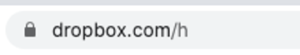
Enabled
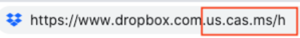
The highlighted section above confirms that the users session is now wrapped and therefore the activities being conducted within the session are being monitored and logged. This will prove pivotal in an investigation carried out by an administrator and allow them to build a timeline of events quickly.
The Benefits of Conditional Access App Control
This CASB solution provides adaptive access control based on the risks we are seeing in real-time for a user. A number of different actions can be set-up using session and access policies [4]:
- Prevent data exfiltration: You can block the download, cut, copy, and print of sensitive documents on, for example, unmanaged devices.
- Protect on download: Instead of blocking the download of sensitive documents, you can require documents to be labelled and protected with Azure Information Protection. This action ensures the document is protected and user access is restricted in a potentially risky session.
- Prevent upload of unlabelled files: Before a sensitive file is uploaded, distributed, and used by others, it’s important to make sure that the file has the right label and protection. You can ensure that unlabelled files with sensitive content are blocked from being uploaded until the user classifies the content.
- Monitor user sessions for compliance: Risky users are monitored when they sign into apps and their actions are logged from within the session. You can investigate and analyse user behaviour to understand where, and under what conditions, session policies should be applied in the future.
- Block access: You can granularly block access for specific apps and users depending on several risk factors. For example, you can block them if they are using client certificates as a form of device management.
- Block custom activities: Some apps have unique scenarios that carry risk, for example, sending messages with sensitive content in apps like Microsoft Teams or Slack. In these kinds of scenarios, you can scan messages for sensitive content and block them in real-time.
MCAS & Conditional Access App Control
Conditional Access App Control provides an additional layer of monitoring and security with no interference to your users BAU tasks. This solution allows you to create a number of session and access policies that will trigger based on the rule conditions configured by an administrator to identify suspicious behaviour. The adaptive access control engine utilises real-time information to decide if a session or access policy is applied, therefore limiting the users’ ability to perform certain tasks. This could prove vital to keeping your data secure.
The next part of this blog series will look at how we can integrate your current DLP policies within MCAS to protect your data from being leaked to an unmanaged device. This will be done via a session policy.
Reference Articles:
[1] https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
[2] https://www.statista.com/statistics/1067748/worldwide-cloud-access-security-broker-market-value/
[3] https://www.microsoft.com/security/blog/2019/10/29/gartner-microsoft-leader-2019-cloud-access-security-broker-casb-magic-quadrant/
[4] https://docs.microsoft.com/en-us/cloud-app-security/proxy-intro-aad
 Meet the Author
Meet the Author
Jordan Candlish, Senior Security Analyst in the Quorum Cyber Managed Services team
“As a professional within the cyber security industry, through practical experience and certifications I have taken a keen interest in cloud security. In particular, Microsoft’s security toolset. This interest is driven not just by my recognition of the growing importance of cloud technologies, but also my passion for protecting organisations from cyber threats.”
For further support from our expert Security Operations Centre and Professional Services teams, contact the Quorum Cyber team today.
