Get in Touch
LockBit ransomware operation disrupted by global law enforcement agencies
Published: 20th February 2024 | In: Insights
On Monday 19th February 2024, the UK’s National Crime Agency (NCA), alongside partner agencies like the FBI, Europol and others, were involved in the globally co-ordinated disruption of the LockBit ransomware infrastructure via the ‘Operation Cronos’ task force. This included the takedown of 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the US, and the UK.
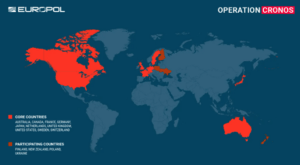
Operation Chronos Global Targeting Profile (Source: Europol).
The seizure notice on the ransomware group’s website stated, “We can confirm that Lockbit’s services have been disrupted as a result of International Law Enforcement action — this is an ongoing and developing operation.”

Operation Chronos Seizure Notice.
In addition to the disruption, the law enforcement agencies also:
- Arrested two LockBit ransomware operators located in Poland and Ukraine
- Retrieved a decryption tool to recover encrypted files for free
- Seized more than 200 cryptocurrency wallets
- Dismantled 34 servers
- Closed 14,000 rogue accounts.
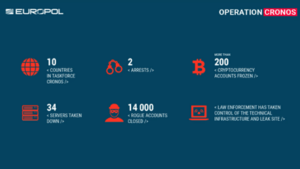
Operation Chronos Global Statistics (Source: Europol).
Key points
- The disruption of the world’s most prominent ransomware group demonstrates the increasing effectiveness of international law enforcement collaboration in combating cybercrimes.
- The operation demonstrates a strategic shift towards disruption and prevention.
- Operation Cronos will likely erode trust amongst cybercriminals, thus inhibiting the wider ransomware ecosystem.
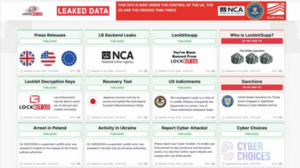
LockBit Leaked Data Site now under the control of the UK, the US, and the Cronos Task Force
Threat actor group
LockBit ransomware is a Ransomware-as-a-Service (RaaS) first detected within the threat landscape in September 2019. The LockBit cartel has emerged as the most active ransomware operation in the world accounting for nearly a third of all reported ransomware attacks globally. Their choice of targeting is diverse and does not focus on a single industry sector, making it challenging to predict their next victim. The LockBit gang has also notoriously recruited affiliates responsible for the deployment of the malware, providing them with the necessary infrastructure and payload builder.
Geopolitical considerations
The LockBit RaaS operation claims to be organised by a cartel with affiliates from a range of international regions, but mostly consists of Russian threat actors. However, it should be noted that Microsoft Threat Intelligence previously verified that Chinese threat actor affiliates, tracked as Storm-0401, are linked with the group. The LockBit ransomware gang has not targeted any organisations in Russia or any other ex-Soviet Union states.
Notably, in November 2023, the Chinese state-owned Industrial and Commercial Bank of China (ICBC) was subjected to a LockBit ransomware attack, with the group also claiming to have compromised China Daily HK in May 2023, an entity owned by the Central Propaganda Department of the Chinese Communist Party (CCP).
Previous intelligence has shown that Chinese nation-state actors have conducted cyber espionage operations against Russian entities. So, there is a realistic possibility that the ransomware attack against the ICBC was a retaliation, with tensions potentially rising between Russia and China.
This represents a potential emerging trend of increasingly blurred lines between financially motivated cybercriminals and nation state-level LockBit operations. It has therefore been assessed that there is a realistic possibility that Operation Cronos could diminish the threat to entities opposed to Moscow.
Outlook
The disruption achieved by Operation Cronos is the latest in a series of law enforcement operations targeting cybercriminal groups, with more recent examples including the takedown of Hive, Qakbot and RagnarLocker infrastructures throughout 2023.
Based on the trends of individual threat actors forming rebranded ransomware operations upon the disbanding of notorious cartels, it has been assessed to be likely that LockBit ransomware operators will return in some form in the near future. However, this serves as a reminder of how the cyber security community can ‘fight the good fight’ by working together to proactively stop cybercrime.
If you would like more details of the LockBit operation, please read the Quorum Cyber Threat Intelligence LockBit 3.0 Ransomware report.

Author
Craig Watt
Threat Intelligence Consultant

