Get in Touch
Law enforcement agencies deny involvement in ALPHV seizure
Published: 7th March 2024 | In: Insights
On Tuesday 5th March 2024, a Federal Bureau of Investigation (FBI) seizure notification appeared on an ALPHV ransomware leak site, leading to initial speculation regarding the disruption of the cartel’s operation.
However, numerous law enforcement agencies, including Europol, the Department of Justice (DOJ) and the UK’s National Crime Agency (NCA) denied involvement in a new notice posted to the ALPHV leak site, seemingly adding legitimacy to speculation within the cyber community the group was attempting to carry out an elaborate exit scam.
This event followed the ALPHV ransomware gang having shut down its servers on 1st March in response to claims that they scammed the affiliate responsible for the ransomware attack on Optum, the operator of the Change Healthcare platform, of $22 million. Upon the affiliate sending the bitcoins to ALPHV, they locked the affiliate out, and shut down their servers, with the affiliate retaining 4TB of Optum’s data. This apparent fraudulent law enforcement seizure, in conjunction with the $22 million theft from an affiliate, indicates the lengths that cybercriminals will go to complete their financially motivated objectives.

FBI Seizure Notice
Confirmation of an exit scam?
On Tuesday 5th March, ALPHV ransomware representatives confirmed on the RAMP cybercrime forum that there is “no point in making excuses” and further stated that they “decided to completely close the project.” In a follow-up statement, the gang’s leaders stated:
“We can officially declare that the feds screwed us over. The source code will be sold, negotiations are already underway on this matter.”
Theft from ransomware affiliates and exit scams are not uncommon within the cybercriminal realm with other prominent operators, such as REvil, doing the same in 2021. This is not the first time that ransomware operators have portrayed apparent takedowns by international law enforcement agencies when attempting to shut down an operation. However, this is the first time that a fake seizure notice has been used, a unique development within the ransomware space, demonstrating the dynamic and deceptive practices within the ransomware ecosystem.
What is ALPHV and who is behind it?
ALPHV is the Russia-based Ransomware-as-a-Service (RaaS) group behind the ALPHV (also known as BlackCat) ransomware operation. As a RaaS, ALPHV will advertise its ransomware on forums soliciting for affiliates. The solicited groups will utilise the ransomware with the agreement that a portion of the extorted ransom goes to the malware authors. Since this gang is dynamic in nature, the tactics and techniques accompanying the deployment of ALPHV ransomware varies in sophistication and extortion techniques.
Alongside the typical threats of data deletion, attackers are known to siphon off data and threaten to release it to the public. Additionally, operators within the ALPHV cartel extort the victim a third time by threatening any third-party suppliers of the primary target. This is followed up by a fourth and final pressure whereby the threat of the implementation of a distributed denial-of-service (DDoS) attack is issued, a combined technique known as the “quadruple extortion method”.
Geopolitical considerations
The ALPHV RaaS operation claims to be organised by a cartel with affiliates from a range of international regions, but mostly consists of Russian threat actors. The ALPHV ransomware gang has not targeted any organisations in Russia or any other ex-Soviet Union states. It has therefore been assessed that there is a realistic possibility that the group’s closure could diminish the threat to entities opposed to Moscow within the ransomware space in the immediate future.
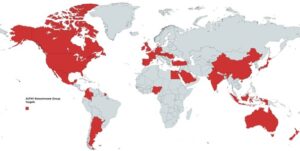
ALPHV Ransomware Global Targeting Profile
What lies ahead?
Even if this has indeed been an elaborate exit scam, the event has exposed the ALPHV leader. Further, based on the trends of individual threat actors forming rebranded ransomware operations upon the disbanding of notorious cartels, it has been assessed to be likely that ALPHV ransomware operators will return in some form soon. However, the exposure of the gang’s deception tactics has severely diminished their reputation and credibility, meaning that any future operations will likely be more challenging to launch.
If you would like more details of the ALPHV ransomware operation, please read the ALPHV Threat Actor Profile – Quorum Cyber.

Author
Craig Watt
Threat Intelligence Consultant

