In this Microsoft Cloud App Security (MCAS) series, we are going to discuss how to configure MCAS and integrate it with some other pre-existing controls to provide rich visibility, complete control over data travel and discover applications that are being used in your enterprise, see figure 1.
In this blog we will be discussing how you can use pre-existing security controls deployed in your environment to enable secure remote working. This will involve using using labels set up within Azure Information Protection (AIP) and integrating these within Microsoft Cloud App Security (MCAS) session and access policies.
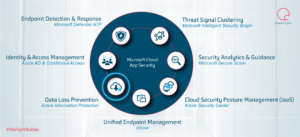
Figure 1: MCAS Components
Enable Secure Remote Working: Do you know where your data is being downloaded?
We have seen a large increase in companies adopting work-from-home strategies to perform their daily BAU tasks during this pandemic. As this has happened suddenly; ensuring users can work securely in a remote setting should be a top priority and extra security measures should be put in place to avoid data leakage.
Azure Information Protection is a cloud-based solution that helps an organisation classify sensitive documents and emails. Labels can be configured and automatically assigned to a document or email based on conditions defined by an administrator. It also has the option to manually assign labels or give users recommendations based on the content identified. Labels have three options, if protection is enabled, it can limit what the recipient can do with these documents, even if it is shared outwith your organisation. This is achieved by using protection technology called Azure Rights Management (Azure RMS) [1].
Two policies can be used to control how a user interacts with these files within the MCAS portal. These are known as session and access policies. For the purpose of this blog, we will focus on session policies and give an example of how your organisation can stop a user from downloading confidential data onto an unmanaged device.
Scenario
A member of the finance team receives a text message from a close colleague whilst at home asking if they would be able to change their banking details that their monthly salary gets paid into. The finance user logs into their Dropbox account using their personal device and tries to download the file to fulfil this request.
If the finance user successfully downloads this document onto their personal device, data has been leaked from the company inadvertently. Forcing the user’s session to go through Cloud App Security Broker will allow the users session to be monitored and restricted.
Mitigating the Scenario Risk: Session Policy
The following steps assume you have already set-up a conditional access policy within Azure AD, using Conditional Access App Control that utilises a custom policy for the application that will be configured within MCAS, this can be seen in Part 2: Conditional Access App Control
This policy will block users downloading documents that have been labelled confidential within Dropbox onto unmanaged devices, see figure 2. This ensures company data is not leaked onto personal devices. It also offers a level of protection if a user account is compromised. No confidential data can be downloaded as they will have an unmanaged device. Although this doesn’t offer a complete solution for a compromised account; this gives another level of protection to your files.
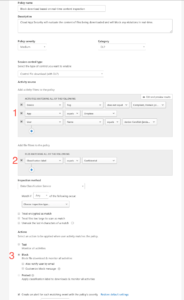
Figure 2 – Session Policy Configuration
Configuration Steps:
- This section has numerous items that need to be configured depending on the controls you wish to set up. This policy is looking for devices that are not compliant or domain joined. The example policy above (fig 2) is looking specifically for the application Dropbox and the users this policy should apply to.
- This policy section was specifically set-up to protect information that is marked as confidential data. Other options in this section can be specific file names or file types.
- This policy section was configured to block the file download if a user matched all of these conditions as we want to prevent data leakage onto an unmanaged device.
Once your policy has been configured, your administrator and end user will see different results when a user matches this policy:
Administrator view
You will notice in figure 2, we checked the box that said create an alert. The administrator will receive an alert to make them aware a user has tried to download a confidential document using an unmanaged device, see figure 3.
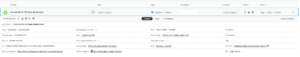
Figure 3 – Session Policy Alert
The alert section shows the administrator an overview of the alert. This shows details such as:
- User who matched this policy
- The file that the user attempted to download
- The Device the user was using
- Date/Time of the alert
The administrator can then navigate to the users activity log to see what other activities the user was conducting, see figure 4.
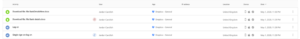
Figure 4 – User Activity Log
The user session was forced through the Cloud App Security Broker, MCAS. This is identified by the label on the single sign-on entry. We can see the user was blocked from downloading “Bank details.docx” but managed to download a file “BankDetailsNew.docx”. The difference between these two files; one had a confidential label attached to the document and matched the policy configured in figure 2. This view allows an administrator to identify other user actions quickly and produce a timelime of user activities.
End-User Experience:
Once the policy has been deployed and the user attempts to download “Bank details.docx”, they will receive a notification informing them this has been blocked by your organisations security policy, see figure 5.
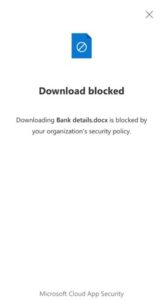
Figure 5 – End-User Delivery Message
The message the user receives is customisable. This allows an administrator to inform them of why the download has been blocked to raise user awareness. As you can see, the user was blocked from downloading confidential data onto an unmanaged device.
Summary
Organisations always try to store data securely and the use of AIP labels achieves this. However, as more organisations adopt an approach to remote working, an administrator needs to be aware of not only what files are being downloaded, but which device these are being downloaded to. Company data should never be downloaded or stored on a personal device and Conditional Access App Controls and MCAS session policies add an extra layer of protection. MCAS achieves this by monitoring the users session and applying configured session policies to restrict user activity. The users are not impacted by these controls unless they do not comply with company policies. This ensures that any document that is listed as confidential within your file sharing application is never downloaded to an unmanaged device.
Reference Articles:
[1] https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection
Meet the Author

Jordan Candlish, Senior Security Analyst in the Quorum Cyber Managed Services team
“As a professional within the cyber security industry, through practical experience and certifications I have taken a keen interest in cloud security. In particular, Microsoft’s security toolset. This interest is driven not just by my recognition of the growing importance of cloud technologies, but also my passion for protecting organisations from cyber threats.”
For further support from our expert Security Operations Centre and Professional Services teams, contact the Quorum Cyber team today.












