Last month, Microsoft announced a rebranding of some well-known products and features under the Microsoft Entra product family. One of the biggest name changes came in the form of Azure Active Directory (Azure AD) being renamed to Microsoft Entra ID. As such, Azure AD Identity Protection was also renamed to Microsoft Entra ID Protection to fall in line with the overall changes. I detailed most of these changes in my last insights entry, and so I want to take the opportunity here to dive deeper into some detailed changes and improvements in the pipeline for Microsoft Entra ID Protection.
By way of introduction, Microsoft Entra ID Protection uses signals to determine whether a user is displaying suspicious sign-in behaviours or generally acting suspiciously. The policies at work can trigger multi-factor authentication (MFA) responses, or even lock users out of key systems altogether. The detail that Entra ID Protection generates can also be helpful to enrich incident information, allowing Security Operation Centre (SOC) teams or automation rules to make more informed decisions.
New dashboard
A huge part of the consolidation work Microsoft has performed is bringing Microsoft Entra ID Protection into the same space as the other security products in Microsoft 365. Before, security analysts had to navigate to the portal.azure.com homepage then use their shortcuts to find Azure AD Identity Protection. Now, it’s been relocated into the entra.microsoft.com portal, with all other technologies and features.

This isn’t just a copy and paste though. This new dashboard contains at-a-glance visualisations so analysts can get immediate insight into potential problems in their identity landscape. This can direct attention to issues quicker, allowing responses to be more decisive.
Take this new attack graphic visualisation as an example:
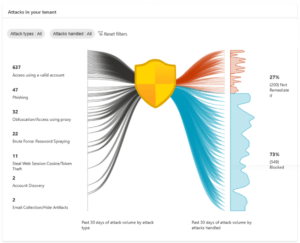
This demonstrates, in a single graphic, all the common identity-based attack patterns targeted at your organisation within the last month and how many were blocked. Again, this focuses an expert’s attention to where it matters, driving more efficient SOC practices.
Finally, within the new dashboard, there’s a new area promoting the top three recommendations that Microsoft Entra ID Protection has to improve your identity security posture.
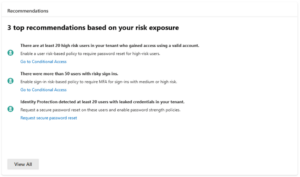
This is a great way of keeping tabs on widespread issues like mass credential leaks.
New detections
As well as changing the look and feel of Microsoft Entra ID Protection to align with the other security products, Microsoft also introduced two new, high-fidelity detections. Here’s a summary of what these new detections monitor for:
Verified threat actor ID: Recently, many major security incidents have been initiated by nation state and cybercrime groups. As one of the largest cyber security companies in the world, Microsoft has created a knowledge base of these actors. If any markers of these attackers are witnessed when signing in, the real-time sign-in risk can be triggered, and access can be denied on-the-fly.
Attacker in the middle: Attackers will often gain access to an environment by using phishing, and a fake login screen to fool users into giving up their credentials. Since the user assumes they’re going through the proper login experience, they’ll often approve MFA requests too, even though the attacker is the one who has initiated this. This new detection uses signals provided by Microsoft 365 Defender and correlates it with Microsoft Entra ID to detect this type of attack. Risk will then be assigned to both the user and the sign-in, triggering Conditional Access policies and allowing customers to revoke the session by requiring a password reset and blocking future use of the compromised credentials.
Real-time threat intelligence
Microsoft Entra ID Protection now offers real-time threat intelligence detections. When new attack indicators of compromise are identified, Microsoft Entra ID Protection can issue new, real-time detections to quickly respond to these emerging threats. Risk based Conditional Access policies will then pick up on this increased risk score and block access accordingly.
Under the risk detection entry, the detection type will show as “Azure AD Threat Intelligence” (a very valid example of the rebranding effort being a process, and not a flipped switch).
Next steps and call to action
Continued convergence of features and functions into Microsoft 365 Defender is a demonstration of Microsoft’s commitment to providing the most complete end-to-end security solutions available on the market. Customers should familiarise themselves with these changes so they can take full advantage of including them in their security arsenal. Of course, as a Microsoft Solutions Partner for Security, you can always ask Quorum Cyber about these feature introductions and discover how they can help keep your identities as safe as possible. Get in touch for more information.












