Get in Touch
Phishing Scams in the Age of COVID-19: Avoid the Traps
Published: 4th May 2020 | In: Insights
The global COVID-19 outbreak is like nothing we have experienced before in our lifetimes. The impacts of the crisis strike across the medical, social, political, and economic aspects of our lives, with no-one left unaffected. Here at Quorum Cyber, we receive reports, investigate various types of threat actors, and address concerns raised in global threat intelligence on a continuous basis.
In this, the time of the COVID-19 crisis, it’s the heightened emotions of the situation that we see many actors taking advantage of – with phishing campaigns being a favourite tactic for malicious parties. So, in the following sections, we’ve laid out information for a wide audience, with the aim of increasing your awareness of how these tactics are deployed, how to report suspicious messages, and how to keep yourself secure online.
COVID-19 Phishing Targets & Statistics
A significant area of concern is the anxiety created by misinformation that surrounds the issue. In the increasingly digital lives we now live, the collective panic and concern leave many vulnerable to potential scams. These vulnerabilities created by challenging and chaotic times have long been enticing targets for hackers. In the time of COVID-19, the most upsetting have been attacks on hospitals and other healthcare services. The majority of these attacks are performed with the use of a social engineering technique called Phishing.
Targeting large and small businesses, charities, government organisations, healthcare institutions, and individuals, phishing scams can take many forms. The most common being fraudulent emails, text messages, and ph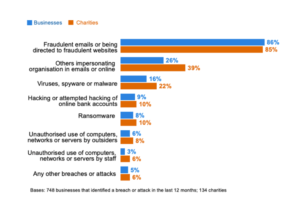 one calls.
one calls.
Phishing is a technique where an email contacting malicious attachment or a link to a malicious website is sent to a person. The content of the message is designed to convince the user to open the attachment or provide personal details. From the most recent Cyber Security Breaches Survey, published by the UK government’s National Cyber Security Centre, we can see that fraudulent emails and the impersonation of organisations in emails are the most common types of attacks.
Although a massive growth of Covid-19 related scams can be observed, some sources point that ‘the level of cybercrime remains the same’. However, it has also been noted that ‘hackers and foreign adversaries are capitalizing on the chaos to extort money and political gain’. [1]
What do phishing emails look like, and what damage can they do?
There is a wide range of damage that a phishing scam can do depending on what the hackers are trying to achieve. This could be to tricking you into providing your login details and passwords, or giving away your bank details. The email might claim that it has a ‘cure’ for the coronavirus or, offer financial help (like VAT return or a benefit/grant), or even to ask for a donation to help relevant charities, the NHS, or vulnerable groups of people. The email might appear as if it’s coming from a legitimate source, using a well know company’s logo, referring to you by name, or perhaps even looking as if it’s coming from a government organization.
Malicious Links
Often, a link in the email will send you to a fraudulent site tailored to look like a genuine website. It might have the same page layout, same pictures and logos as the genuine website that it’s imitating. You would be surprised how easy it is to copy a website.
Examples of phishing messages have been published by the government:
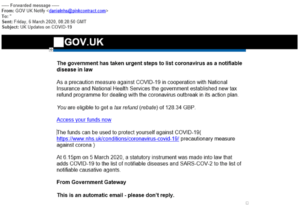
The example above shows an email tailored to look as if it’s coming from the government, informing the recipient of an entitlement for a tax refund. Looking at the source of the message, it can be seen that – although the name of the account is set up as ‘GOV UK Notify’ – the actual originating email address is not from a government domain, but rather @pinkcontract.com.
The ‘Access your funds now’ link will take you to a fraudulent website:
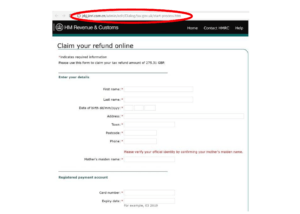
In the above screenshot, we can see that the fraudulent website is a very effective copy of the actual HMRC website – with similar colours, layout and logo. However, looking at the address link bar (circled in red) we can see that it is, in fact, a fraudulent website.
Please note that before clicking on any links provided on websites or in messages it is’s recommended to hover your cursor over the link, without clicking on it.
A small pop up window will appear just above your cursor, showing what is the exact URL that the link will be redirecting us to.
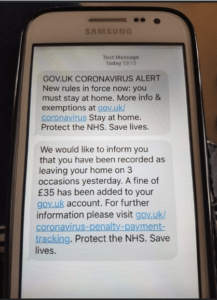
Similar scam messages have also been sent by text message:
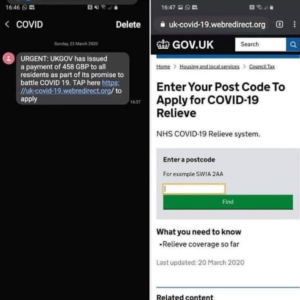
In both of the above examples, the phishing messages are trying to redirect recipients to fraudulent websites in order to obtain personal information and bank details.
In some cases, a phishing message could be trying to get our phone numbers or user account details (username, password, recovery question details). This example of a phishing message has been posted by Microsoft on their Twitter account:

A stolen password might be used to hack a person’s accounts. Please take a minute to think of how often you reuse the same password and email address for different sites, and what information those sites contain. It may be your card details, PayPal account details, home address, phone number, personal details, pictures, and/or sensitive documents. Attackers will often use a compromised password with slight variations across other online services in order to gain further access into a user’s online presence.
Malicious Content & Attachments
Phishing emails may also have malicious content, so when you open a link or attachment malicious software gets installed on your computer. Two main types of malicious software, and their effects, include:
- Software that quietly runs in the background of your computer without you knowing about it, tracking what sites you visit, and noting your login details for those sites, or stealing credentials stored by legitimate applications installed on your computer, such as web browsers.
- Ransomware that locks your computer and data within it, asking for money to be paid in order to recover the data.
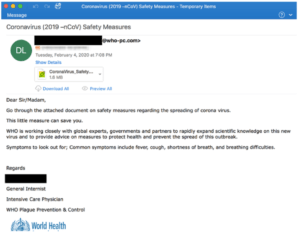
Below, we can see a phishing email with a malicious attachment, originating from an email address with the @who-pc.com domain, and using the World Health Organisation (WHO) logo:
Social Engineering Tactics & Techniques
Phishing employs persuasive tactics and techniques, convincing victims to provide information or open malicious content. These techniques include:
- Authority – the sender claims to be someone official and important, such as the target’s GP, bank, the HMRC or government, etc.;
- Urgency – the victim is told that action must be taken immediately; for example, to take advantage of a flash sale or to pay an outstanding invoice as legal actions have been taken;
- Emotion – situations that make people upset or emotional might make them do something they might otherwise not do (e.g. make a donation) are taken advantage of with emotional appeals from the sender;
- Scarcity – in present circumstances, it might be a message offering purchase of PPE equipment, hand sanitiser, or even access to testing for the virus;
- Current events – it might be an email advising to visit a site for a recent COVID-19 update, or prompting the recipient to follow a link to apply for a grant that has been launched by the government.
In a way, the phishing messages being used to target us are just like a Pandora’s box. The curiosity which entices victims to open them unwittingly unleashes stress and upset, utilising and amplifying the very stresses that make targets vulnerable. Particularly in times of community distress, like the COVID-19 outbreak.

Word cloud showing the most frequently occurring words in the phishing email subject lines [2].
What can you do as an individual to keep yourself and others safe from phishing scams?
First, be vigilant.
Carefully inspect all received emails. A good starting point is to look at the email address that the email is coming from. As in the examples above, it’s very easy to impersonate an organization or copy a logo.
If an email is received from a bank or any organization asking for your personal details or for a payment, contact the bank or organisation directly using the contact details provided on their website – not in the suspicious email – and verify this information.
Second, don’t click.
Do not open any attachments or click on any links if you find anything about the email suspicious. Before opening an attachment hover your cursor over the link – without clicking on it – to make sure it’s taking directing to the site it’s meant to:
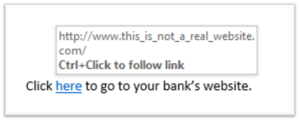
Hover your cursor over the link, without clicking, to see the directed link.
Third, report any suspicious messages.
The National Cyber Security Centre is urging everyone to flag any Covid-19 threats by forwarding all suspicious emails to [email protected]. This will allow cyber specialist to investigate the source of the fraudulent message, flag it as a threat, and remove any malicious website associated with the threats identified.
Report any online shopping fraud to Action Fraud. Also remember to inform the bank, business or charity that a phishing message was received that has been impersonating them.
What should you do if you already opened a malicious attachment or provided personal information?
If you were using a company device, please contact your the company’s IT department immediately, and follow their advice.
If there is an antivirus software installed on the device, run a full scan for it to find and fix issues.
If there is no antivirus installed on the device, there are free antivirus options available to run online (for example HouseCall by Trend Micro) or download and install on your device (for example Avast).
If there are suspicions that an account has already been hacked:
- Change the compromised account password;
- Set up two-factor authentication (2FA) on your accounts. Websites such as https://twofactorauth.org/ are available for assistance in setting up 2FA;
- Update your device to the latest version (updates usually fix security vulnerabilities and sometimes perform scans);
- Contact your account provider (for example for an online shopping account contact the retailer);
- If an email account has been hacked, remember to inform your contacts – fraudulent emails may be sent from the your account to addresses in your contact list.
For more information on how to deal with hacked accounts, please follow the National Cyber Security Centre’s advice on how to recover an account.
If you have provided your bank details, immediately contact your bank to notify them and cancel or freeze any affected debit or credit cards.
If you’ve provided your password, please immediately change your password on any account/website that was using this password.
For more information on cyber security and phishing scams please refer to the National Cyber Security Centre’s website. It will provide you with news and guidance on how to use your devices securely.
For advice on or to report an online shopping fraud, please visit Action Fraud.
How can you protect your business from phishing threats?
Working closely with client organisations across sectors, the Quorum Cyber team actively develops proactive approaches that safeguard businesses and teams against cyber security threats, such as those posed by attackers employing phishing tactics.
Quorum Cyber’s Phishing Simulation Platform enables organizations to regularly assess their resilience to phishing attacks, and measure the impact of their cyber security awareness investment over time, by launching advanced phishing campaigns against their users. Ranging from Social Media and High Street Banks impersonations all the way to internal looking customised internal company templates, we drive security awareness by providing constant tests and knowledge reinforcements to users.
Quorum Cyber’s Phishing Protection service and tool provides a simple way for users to verify if a suspicious-looking email is malicious, without having to rely on their own technical knowledge. By simply clicking on the Big Red Button Outlook plugin, our platform can help protect your users from malicious email attacks such as phishing and ransomware, enabling us to identify any malicious activity within a safe environment, and providing simple actionable advice for your users to keep your organisation protected.
For further support from our expert Security Operations Centre and Professional Services teams, contact the Quorum Cyber team today.
Links to Resources:
[1] Lucas Ropek (2020). “Hackers Have Been Waiting for an Opportunity Like Coronavirus.” Available online at Government Technology.
[2] Ferreira, A., & Teles, S. (2019). “Persuasion: How phishing emails can influence users and bypass security measures.” Available online at International Journal of Human-Computer Studies.
