Get in Touch
Please get in touch using the form below.
Microsoft Cloud App Security (Part 1): Microsoft Defender ATP
Published: 24th June 2020 | In: Tech Blog
In this Microsoft Cloud App Security (MCAS) series, we are going to discuss how to configure MCAS and integrate it with some other pre-existing controls to provide increased visibility, complete control over data travel between applications and devices and application discovery within your enterprise (see figure 1).
In this blog, we will be discussing how to integrate MCAS with Microsoft Defender ATP (MDATP) and configure a feature that was released in February 2020: Blocking unsanctioned apps with MDATP.
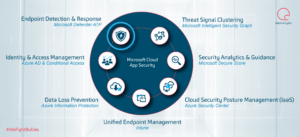
Figure 1: MCAS Components.
Shadow IT: What Applications are Your Employees Using?
Enterprises struggle to find the balance between supporting access whilst maintaining control to protect confidential data. The purpose of this blog post is to show how you can do exactly that, all whilst controlling which applications users are allowed to use within your organisation. IT admins will largely underestimate how many applications are within their environment. On average most say 30 or 40 when, in reality, the average is over 1000(1). It has been found that a number as high as 80% of users within your organisation could be using non-sanctioned apps that may not be compliant with your organisation’s security and compliance policies [1].
Microsoft Defender ATP (MDATP)
MDATP is normally used by many organisations as an anti-virus solution, detecting when a malicious file or script has been run on an end-user device.
It currently boasts nine different security features that IT admins can make use of. These include Vulnerability Management, Endpoint Detection and Response, Secure Score amongst others. One feature that we are interested in is Microsoft Threat Protection. MDATP is built to integrate with other security components in Microsoft’s Threat Protection solution to try and achieve end-to-end security [2]. This means an enterprise can secure communication and data travel between applications and employees. One of these components that it collaborates with is MCAS.
Microsoft Cloud App Security (MCAS)
MCAS was released in 2018. The purpose of this tool is to act as a cloud app security broker (CASB) and provide rich visibility into application usage, malware infection vectors, and much more.
Alerts and policies can be configured to trigger against specific user activity if the application is configured to use the CASB. This enables you to determine how your data travels outwith your organisation and which devices are allowed to download company files. This is one example of many. MCAS also provides sophisticated analytics to identify and combat cyber threats.
Once MCAS is connected your applications, using an app connector, MCAS scans all the files stored in your businesses file storage solution, for example, Dropbox or OneDrive. Each time these files are modified, MCAS will rescan them.
For more information on licensing, please refer to the Microsoft Cloud App Security licensing guide at www.aka.ms/mcaslicensing
Discover Shadow IT
The term ‘Shadow IT’ is not a new term, although it is an emerging threat as more and more organisations move into the cloud. This is simply the use of an application or service within an organisation that has not been approved by an IT team. They are under extreme pressure, more than ever, now most companies have been forced to remote working, to understand which applications are being used in their environment.
MCAS has a multi-layered lifecycle on its security deployment to managing this threat (see figure 2).
Figure 2: MCAS Security Deployment
Requirements:
- Integrate MDATP and MCAS: Navigate to the MDATP portal, at the bottom of the left side panel, click on settings and advanced features and click on the toggle bar, (see figure 3).

Figure 3: MDATP & MCAS Integration
- Enable custom network indicators: Still within MDATP portal, locate the below setting to switch this on (see figure 4).

Figure 4: Enable Custom Network Indicators
- Turn on Cloud App Control: Navigate to the MCAS portal, on the top right click on settings, under the cloud discovery column, click on Cloud app control and check the box (see figure 5).
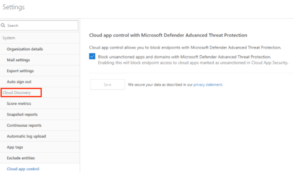
Figure 5: Enable Cloud App Control
It’s important to note at this stage that any unsanctioned applications already in the organisation will be marked as blocked at your end points.
This may cause some issues with end users. This feature is only currently available for Windows 10 machines; however, it is on their roadmap to extend this feature to other operating systems such as MacOS.
Configure Unsanctioned Apps
Now you are monitoring user applications on your MCAS dashboard, we can view discovered apps within your estate (see figure 6).
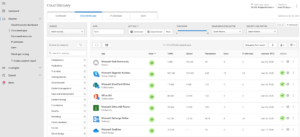
Figure 6: Cloud App Discovery
Marking an application as unsanctioned can be done in two methods, manually or automatically, by setting up a policy.
Manual Configuration
Go to your cloud app dashboard (Figure 6), click on the application you want to mark as unsanctioned and select unsanctioned (see figure 7).
![]()
Figure 7: Unsanctioned Application
Automatic Configuration
Marking applications automatically can be done by configuring an app discovery policy. Below we see any application with a risk score lower than 4 being marked as unsanctioned automatically, therefore blocking users using this application anymore (see figure 8).
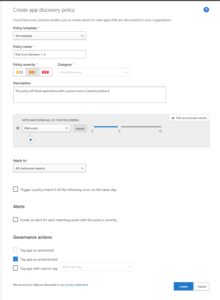
Figure 8: App Discovery Policy
Manual vs. Automatic Configuration
The preferred method of configuration is manual. The reason for this is; the risk score of an application is measured by 70 different risk factors which are measured in four different categories [3]:
- General – This category refers to basic facts about the company that produces the app, including its domain, founding year, and popularity. These fields are meant to show the company’s stability on the most basic level.
- Security – The security category accounts for all standards dealing with the physical security of the data used by the discovered app. This category includes fields such as multi-factor authentication, encryption, data classification, and data ownership.
- Compliance – This category displays which common best-practice compliance standards are upheld by the company that produces the app. The list of specifications includes standards such as HIPAA, CSA, and PCI-DSS.
- Legal – This category displays which apps have which regulations and policies in place to ensure data protection and privacy of the app’s users such as GDPR, DMCA, and data retention policy.
Risk scores can be adapted to your organisation’s needs. You can also override the decision given by the portal if you know this application is used within your organisation and managed properly.
Outcome
Once the application is marked as unsanctioned, MCAS and MDATP exchange data and custom indicators will be populated. These can be found in the MDATP portal, Settings > Indicators > URLs/Domains. As Facebook was marked as unsanctioned, this indicator was added to MDATP automatically (see figure 9).
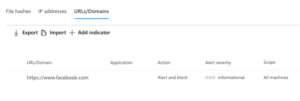
Figure 9: Custom Indicator List
The user will receive an error message now when they try and navigate to this site informing them it has been blocked by an administrator. This data is normally populated within minutes of it being marked as unsanctioned and protected by the Network Protection SLA [5].
MCAS & Defender ATP: Managing Risk in Your Organisation
MCAS allows you to see the applications used within your organisation and how many users are currently using it. Furthermore, the risk score allows you to determine how compliant this application is with your security and compliance policies. This recent feature, blocking unsanctioned applications, allows IT teams to quickly and effectively stop users globally from using these at the endpoint if they are found to be inadequate or suspicious and more importantly protect confidential data.
If you would like unsanctioned applications to only be available to a certain group of users, this can be achieved by using Conditional App Access Control. Blocking unsanctioned applications should be used mainly for banned or rogue applications found within your organisation.
Shadow IT accounts for around 30-40% of IT spending in large enterprises as around 83% of staff admit to using unsanctioned applications in their cloud environment [5] (see figure 10).
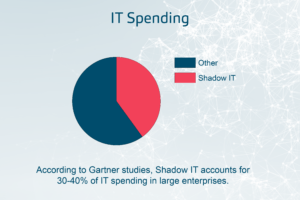
Figure 10: Shadow IT Spend
Different types of applications, oAuth applications for example, provide an extra risk as they use existing credentials along with permissions which widen the attack surface. Whilst unsanctioned applications provide a challenge for IT teams, MCAS provides the IT teams with a centralised dashboard to view all the applications in use within your organisation, along with the integration to MDATP, enabling them to go one step further and block this activity.
The next part of this series will take a look at deploying conditional access app control for any application within your environment.
Reference articles:
[1] https://docs.microsoft.com/en-us/cloud-app-security/tutorial-shadow-it
[2] https://searchsecurity.techtarget.com/definition/Windows-Defender-Advanced-Threat-Protection-ATP
[3] https://docs.microsoft.com/en-us/cloud-app-security/risk-score
[4] https://docs.microsoft.com/en-us/cloud-app-security/wdatp-integration
[5] https://www.cloudcodes.com/blog/what-is-shadow-it-and-its-impacts.html
Meet the Author

Jordan Candlish, Senior Security Analyst in the Quorum Cyber Managed Services team
“As a professional within the cyber security industry, through practical experience and certifications I have taken a keen interest in cloud security. In particular, Microsoft’s security toolset. This interest is driven not just by my recognition of the growing importance of cloud technologies, but also my passion for protecting organisations from cyber threats.”
For further information on the support our Security Operations Centre & Consulting teams can provide you and your organisation, contact the Quorum Cyber team today.
